Top Security Measures for Protecting Your Cloud Computing Server Environment
As Top Security Measures for Protecting Your Cloud Computing Server Environment takes center stage, this opening passage beckons readers into a world crafted with expertise, ensuring a reading experience that is both absorbing and distinctly original.
Cloud computing has revolutionized the way businesses operate, offering scalability, flexibility, and cost-effectiveness. However, with great power comes great responsibility, and securing your cloud computing environment is paramount. This comprehensive guide delves into the top security measures you need to implement to safeguard your valuable data and infrastructure.
Network Security Measures
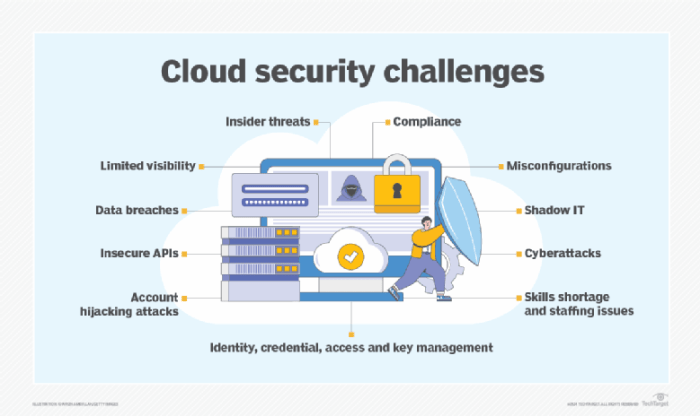
Network security measures are crucial in protecting cloud computing server environments from unauthorized access, malicious attacks, and data breaches. Implementing robust network security controls ensures the confidentiality, integrity, and availability of data and resources stored in the cloud.
Firewalls, Top Security Measures for Protecting Your Cloud Computing Server Environment
Firewalls are network security devices that monitor and control incoming and outgoing network traffic based on predefined security rules. They act as a barrier between the trusted internal network and the untrusted external network, blocking unauthorized access to critical resources.
Intrusion Detection Systems (IDS)
Intrusion detection systems (IDS) continuously monitor network traffic for suspicious activities and security threats. They analyze network packets, identify patterns of malicious behavior, and generate alerts when potential attacks are detected.
Intrusion Prevention Systems (IPS)
Intrusion prevention systems (IPS) go beyond detection by actively blocking malicious traffic. They work in conjunction with IDS to prevent unauthorized access, denial-of-service attacks, and other security threats.
Network Segmentation
Network segmentation involves dividing the cloud network into multiple isolated segments or subnets. This technique helps contain the impact of security breaches by limiting the access of attackers to specific segments. Critical resources and sensitive data can be isolated in separate segments with restricted access.
Monitoring and Analysis
Continuous monitoring and analysis of network traffic is essential for detecting and responding to security threats promptly. Security teams should monitor network logs, traffic patterns, and system events to identify anomalies, investigate potential threats, and take appropriate mitigation actions.
Summary: Top Security Measures For Protecting Your Cloud Computing Server Environment
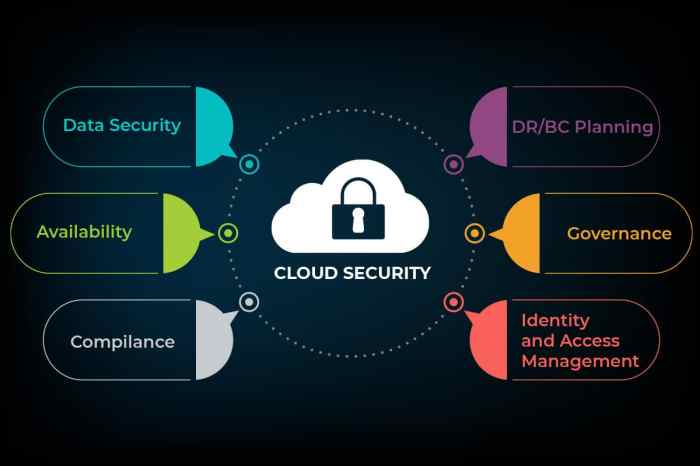
In conclusion, implementing these top security measures is crucial for protecting your cloud computing server environment from a myriad of threats. By embracing encryption techniques, access control mechanisms, network security measures, security monitoring and logging, and vulnerability management, you can create a robust and secure foundation for your cloud infrastructure. Remember, cloud security is an ongoing journey, and staying vigilant and adapting to evolving threats is essential. By following these best practices, you can ensure the confidentiality, integrity, and availability of your cloud-based assets.
.gallery-container {
display: flex;
flex-wrap: wrap;
gap: 10px;
justify-content: center;
}
.gallery-item {
flex: 0 1 calc(33.33% – 10px); /* Fleksibilitas untuk setiap item galeri */
overflow: hidden; /* Pastikan gambar tidak melebihi batas kotak */
position: relative;
margin-bottom: 20px; /* Margin bawah untuk deskripsi */
}
.gallery-item img {
width: 100%;
height: 200px;
object-fit: cover; /* Gambar akan menutupi area sepenuhnya */
object-position: center; /* Pusatkan gambar */
}
.image-description {
text-align: center; /* Rata tengah deskripsi */
}
@media (max-width: 768px) {
.gallery-item {
flex: 1 1 100%; /* Full width di layar lebih kecil dari 768px */
}
}
To ensure the highest levels of protection for your cloud computing server environment, implementing robust security measures is paramount. However, determining the most appropriate cloud server type for your specific needs is also crucial. By understanding the distinctions between public and private cloud servers ( Public vs.
Private Cloud Servers: Which Cloud Computing Server is Right for You? ), you can make an informed decision that aligns with your security requirements and business objectives. This comprehensive guide explores the key considerations to help you choose the optimal cloud server solution while maintaining the highest levels of security for your critical data.
To ensure the security of your cloud computing server environment, implementing robust measures is crucial. Learn more about the latest advancements in cloud computing server management by exploring our article on Cloud Computing Servers: Revolutionizing Enterprise Data Management . Discover how these advancements can enhance the protection of your sensitive data in the cloud.
Implementing top-notch security measures is crucial for safeguarding your cloud computing server environment. As businesses embrace cloud computing for its enhanced scalability and flexibility, it’s essential to consider how cloud computing servers enhance scalability and flexibility . By seamlessly integrating these measures into your cloud infrastructure, you can ensure both optimal performance and robust protection against potential threats.