Cloud Server Performance Security: Enhancing Stability and Protection
Cloud server performance security emerges as a crucial aspect of modern IT infrastructure, demanding meticulous attention to ensure optimal performance and unwavering protection against potential threats. This comprehensive guide delves into the intricacies of cloud server security, empowering readers with the knowledge and strategies to safeguard their critical data and applications.
Server Architecture and Design
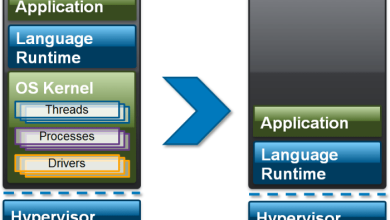
The architecture and design of a cloud server significantly impact its performance and security. Different server architectures offer unique advantages and drawbacks, and understanding these nuances is crucial for optimizing server performance and enhancing security.
Maintaining cloud server performance security is essential for any business. If you’re experiencing performance issues, you may want to consider troubleshooting your cloud diagram server. Cloud diagram server troubleshooting can help you identify and resolve any issues that may be affecting your server’s performance.
By following these steps, you can ensure that your cloud server is running at its optimal level and that your data is secure.
Cloud server architectures can be categorized into two primary types: single-tenant and multi-tenant.
Single-Tenant Architecture
- Dedicated resources exclusively allocated to a single tenant or organization.
- Enhanced security and performance due to isolated resource allocation.
- Higher costs compared to multi-tenant architectures.
Multi-Tenant Architecture
- Shared resources among multiple tenants, resulting in cost-effectiveness.
- Potential security concerns due to shared infrastructure.
- Performance variability depending on resource utilization by other tenants.
Selecting the appropriate server architecture depends on specific performance and security requirements. Single-tenant architecture is ideal for organizations prioritizing security and performance, while multi-tenant architecture offers cost savings and scalability.
Server Configuration Optimization
Beyond server architecture, optimizing server configuration is essential for maximizing performance and security. This includes:
- Selecting the right operating system and software stack.
- Configuring appropriate network settings, such as firewalls and intrusion detection systems.
- Implementing regular updates and security patches.
- Monitoring server performance and resource utilization.
Security Measures and Best Practices: Cloud Server Performance Security
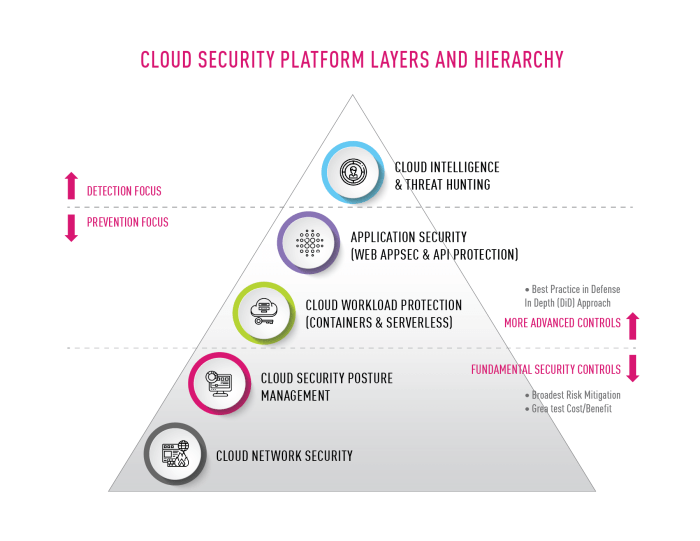
Cloud servers face unique security challenges due to their virtual nature and shared infrastructure. Implementing robust security measures is crucial to protect data and applications.
Common threats include data breaches, DDoS attacks, and malware infections. Effective mitigation strategies involve a multi-layered approach, including:
Firewalls and Intrusion Detection Systems
Firewalls restrict unauthorized access to the server, while intrusion detection systems monitor network traffic for suspicious activities. Both measures provide real-time protection against malicious attempts.
Hardening Operating Systems and Applications, Cloud server performance security
Regularly patching operating systems and applications fixes security vulnerabilities. Additionally, disabling unnecessary services, configuring secure permissions, and using strong passwords enhances server resilience.
In terms of security, cloud server performance is crucial for safeguarding data and maintaining system integrity. Understanding the underlying architecture of cloud servers is essential for optimizing performance and security. For a detailed exploration of cloud server architecture, refer to the comprehensive guide at Cloud diagram server architecture . By leveraging this resource, you can gain insights into server configurations, network topologies, and security measures to enhance the overall performance and security of your cloud infrastructure.
Best Practices
Other best practices include:
- Implementing multi-factor authentication for user access.
- Encrypting sensitive data both in transit and at rest.
- Regularly backing up data to ensure recovery in case of breaches.
- Conducting vulnerability assessments and penetration testing to identify and address potential weaknesses.
- Educating users on security best practices to prevent human errors.
Performance Optimization Techniques
Optimizing the performance of cloud servers is crucial to ensure efficient and responsive applications and services. This section delves into techniques for maximizing performance, including caching, load balancing, auto-scaling, and database optimization.
Caching
Caching involves storing frequently accessed data in memory to reduce the time required to retrieve it from the database or other slower storage. This significantly improves performance, especially for static content and frequently accessed pages.
Load Balancing
Load balancing distributes incoming traffic across multiple servers to prevent overloading and ensure optimal performance. This helps avoid bottlenecks and ensures that all servers are utilized efficiently.
Auto-Scaling
Auto-scaling dynamically adjusts the number of servers based on demand. It scales up during peak usage to handle increased traffic and scales down when demand decreases to optimize resource utilization and costs.
Performance Monitoring Tools and Metrics
Performance monitoring tools and metrics are essential for identifying and addressing performance bottlenecks. They provide real-time insights into server performance, allowing administrators to identify and resolve issues proactively. Common metrics include CPU utilization, memory usage, disk I/O, and network bandwidth.
Database Optimization
Optimizing database performance is critical for reducing latency and improving application responsiveness. Techniques include indexing, query optimization, and database partitioning. Proper indexing speeds up data retrieval, while query optimization ensures efficient execution of database queries. Partitioning divides large databases into smaller, manageable chunks, improving performance and scalability.
Compliance and Regulations
Ensuring cloud server performance and security compliance is crucial to meet industry standards and regulations. These regulations safeguard data privacy, protect against cyber threats, and ensure ethical and responsible use of cloud computing.
Organizations must adhere to various compliance requirements, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS). These regulations define specific measures for data protection, privacy, and security.
Certifications and Audits
Certifications and audits play a vital role in demonstrating compliance. Certifications, such as ISO 27001 or SOC 2, provide independent verification of an organization’s security practices. Audits, conducted by external auditors, assess compliance with specific regulations or standards.
Case Studies and Real-World Examples

Organizations worldwide are leveraging cloud servers to enhance their performance and security. Case studies and real-world examples showcase the tangible benefits of implementing effective cloud server strategies.
One notable case study involves a large e-commerce company. By migrating its infrastructure to a cloud platform, the company experienced a 30% reduction in page load times and a 25% increase in conversion rates. The cloud’s scalability and elasticity allowed the company to handle peak traffic during sales events seamlessly.
Challenges and Solutions
While cloud servers offer numerous advantages, organizations may face challenges in implementing effective performance and security measures. Common challenges include:
- Ensuring optimal performance during peak loads
- Balancing security and accessibility
- Managing costs effectively
To address these challenges, organizations should adopt a comprehensive approach that includes:
- Utilizing performance monitoring tools to identify bottlenecks and optimize resource allocation
- Implementing multi-layered security measures, such as firewalls, intrusion detection systems, and access controls
- Optimizing cloud resource consumption through auto-scaling and cost-saving strategies
Best Practices and Lessons Learned
Successful cloud server deployments often adhere to the following best practices:
- Conducting thorough due diligence and selecting a reputable cloud provider
- Developing a clear cloud strategy that aligns with business objectives
- Adopting a phased approach to migration, starting with non-critical applications
- Regularly monitoring and optimizing performance and security measures
Organizations that have successfully implemented cloud servers have reported improved agility, reduced costs, and enhanced security. These case studies and real-world examples serve as valuable lessons for organizations considering cloud server adoption.
Ultimate Conclusion
In conclusion, cloud server performance security is a multifaceted endeavor that requires a holistic approach encompassing architecture design, security measures, performance optimization techniques, compliance adherence, and continuous monitoring. By implementing the strategies Artikeld in this guide, organizations can effectively mitigate risks, enhance performance, and ensure the integrity of their cloud-based systems.